Elusive Facebook Phish
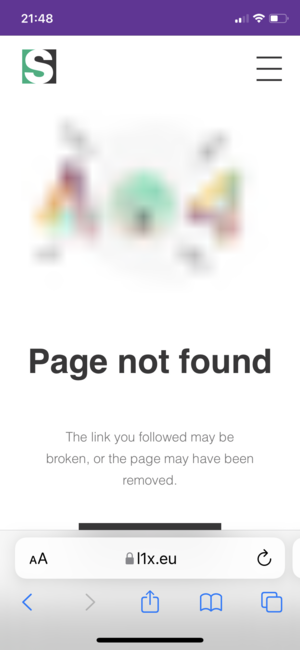
Phishing FacebookRecently I received a spam message from a Facebook friend of mine whose account had been compromised. I immediately spotted the scam by the style of delivery and reported it to Netcraft. I was intrigued to find more about the phish, so I visited it again. However this time I was presented with code 404 “page not found” - the difference being I had visited the phish from the full Safari browser rather than the built-in version within the Messenger app…
The phish was obviously using some technique to detect the environment, with the aim of being more elusive to avoid detection, and thus only served content in the situation where it was likely being accessed by a potential victim. Before I reveal how it does this lets talk about…
The Phish’s M.O.
Which is as follows:
- Receive the message: Is this you in the video?!
https://l1x[.]eu/j8eDymnUNh - The message compels you click link and the shortness of the link makes me thing that the site is a third party content platform.
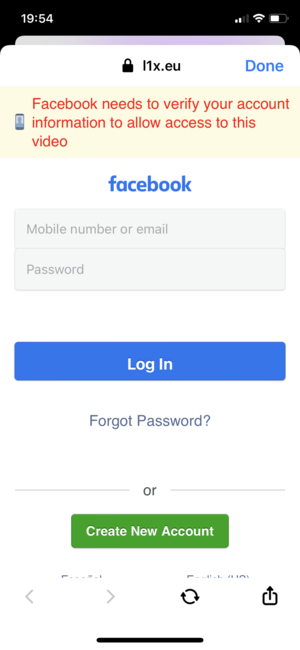
- You are then greeted by a Facebook login page. It’s not particularly obvious that the form isn’t real due to it being opened up in the in-app browser.
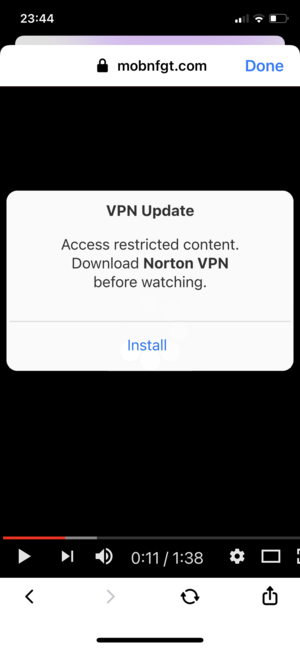
- If you were to take the bait and enter your credentials then you would be redirected to one of many possible destinations: Links to install a VPN (likely malware), fake “your device has been compromised pages” or survey scams.
How the phish avoids detection
When a browser makes a connection to a site it sends various bits of data to the site. One of those is called the User-Agent which typically contains: details about the device, the browser being used…
Mozilla/5.0 (iPhone; CPU iPhone OS 14_8 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Mobile/15E148
When using the inbuilt Safari browser in Facebook Messenger it appends additional information relating to the App and
more details about your device: (LightSpeed [FBAN/MessengerLiteForiOS;FBAV/335.1...). However, this behaviour
ultimately reveals to the malicious actor that the site is being viewed through Messenger and so they should serve you
the Facebook Phish.
Below are some examples of these extended User-Agents…
Mozilla/5.0 (iPhone; CPU iPhone OS 14_8 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Mobile/15E148 LightSpeed [FBAN/MessengerLiteForiOS;FBAV/335.1.0.54.71;FBBV/327105523;FBDV/iPhone10,6;FBMD/iPhone;FBSN/iOS;FBSV/14.8;FBSS/3;FBCR/;FBID/phone;FBLC/en-GB;FBOP/0]
Mozilla/5.0 (iPad; CPU OS 15_1 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Mobile/15E148 LightSpeed [FBAN/MessengerLiteForiOS;FBAV/335.1.0.54.71;FBBV/327105523;FBDV/iPad14,1;FBMD/iPad;FBSN/iOS;FBSV/15.1;FBSS/2;FBCR/;FBID/tablet;FBLC/en-GB;FBOP/0]
But why?
Evading detection makes life more difficult for parties who might be able to take action against the site (and ultimately getting it removed) which prolongs the time the site is active and therefore can steal credentials from victims.
Automated systems that classify possibly malicious URLs are unlikely to visit the site with a Messenger-esk User-Agent and therefore would need manual intervention to confirm the phish exists. The User-Agent requirement puts up a barrier at each stage of the identification and reporting process. Entities like the host or registrar will need to independently confirm the fraudulent content exists and come to the same conclusion about the site.
To the outside world this site l1x[.]eu just looks like an instance of short.io’s URL shortener
software with no active links, when in fact the entire domain been purpose registered (on the 30 July 2021 with
NameCheap) to host these Facebook phish.
Subtle giveaways which identify a phish
Signs to help you avoid falling for such scams.
- Generic initial message - Does this Facebook friend message you often, how do they typically form their messages?
- Unfamiliar domain in the link - You should immediately be wondering what this site is and be suspicious
- Facebook Login form not on facebook.com - Always check the domain. Even third-party apps requesting permission to use your Facebook account will always go through facebook.com not their domain.
- Use of imperative text - Designed to force you to take quick action without thinking “Facebook needs”
- Incomplete site - If trying to navigate to other pages results in errors or broken looking pages this is indicative of phishing